Cuckoo’s Egg

- Author: Clifford Stoll
- Blog Post: 2022-07-31 - The Cuckoo’s Egg
- Newsletter Posts: https://cybersecurityhour.com/t/the-cuckoos-egg
Notes
Chapter 1
- Cliff is an astronomer at the Kent Observatory at the Lawrence Berkeley lab, in an academic dreamland. But funds run out and instead of letting him off he is transferred to the computer center. He is grateful that he has a job instead of having to stand on the unemployment line.
- His neighbors - Wayne an expert who complains and Dave, a Unix Buddha. They manage the computers used by the lab employees.
- On the second day, Dave hands Cliff a problem of a 75 cent shortfall in the last month’s bill or server usage.
- After trying several programs and trial and error, Cliff finds that a user named Hunter had used a server for some time. It was not accounted for since Hunter was not added to the system. He thought the problem is solved.
- Next day they received an email from a computer named Dockmaster saying that their computer was broken into. While investigating this Cliff finds that a user named Sventek had logged in.
- But Dave says it could not have been Joe Sventek since he had left for England last year.
Chapter 2
- A week later Sventek logs in again.
- Cliff talks about account types, privileges, people hacking for fun, etc. Could the movie Wargames actually happen? (Reminds me.. I’ve got to watch this! I’ve come across mentions of the movie earlier too.)
- Cliff wonders if the user who is accessing the labs computers could be a super-user hacker.
Chapter 3 & 4
- Interesting tidbit - Lawrence Berkeley lab and Lawrence Livermore lab - both were named after California’s first Nobel Laureate.
- Cliff and Dave go to Rory who is their division head and talk about the hacker. He asks them to find proof.
- Cliff writes a program to beep his terminal whenever someone connected to the Unix computer and finds out which port the hacker connector from - tt23. “tt” - dial-in telephones.
- He decides to printout commands issued by the hacker when they log in. Borrows around 50 printers and portable devices from others. Next morning, finds eighty feet of printout!
- Stoll says the hacker had exploited a vulnerability in the Gnu-Emacs editor, which enabled him to move a file to protected systems area and execute atrun program. He likens this to a cuckoo laying its egg in another bird’s nest. Once inside, the hacker was reading emails, exploring the lab’s network, and accessing other connected computers, all the while constantly checking for system changes to look for signs of whether he was being monitored. Stoll realizes that he needs to be more subtle in his monitoring.
Chapter 5
It is Cliff’s second week at the job. He writes notes about the weekend activity of the hacker. The division chief, Roy, comes around asking for details to know if the hacker caused any damage. Cliff says that the hacker is a super user and can potentially delete everything they have or infect the computers with viruses or other malware. They consider patching the vulnerability and locking the hacker out. But, though that might protect them in the short term, without knowing who the hacker is, they might be at risk of the hacker finding another way to break in. Cliff thinks it might be a college student, but Roy dismisses that since they could connect directly. In the end, Roy says this is ‘electronic terrorism’ and asks Cliff to use all the resources they have to catch the hacker and gives him three weeks.
Cliff’s quote - “The astronomer’s rule of thumb: if you don’t write it down, it didn’t happen.”, made me wonder if taking notes is more natural to people in the sciences. Do researchers and academics take more notes than people in other fields - say sports, politics, etc? Not quite, I guess. Note taking is valuable in any field, and famous people like Ben Franklin did have a regular habit of taking notes.
Chapter 6
Cliff reflects on his relationship with Martha, on how she is the only person with whom he has had a relationship for more than two years. He likes the freedom of live-in rather than the tie-up of marriage. He wonders if this investigation would impact the relationship since he is spending all the time there, including sleeping. At the office, they decide to set up a new Unix-8 computer where data can come in but not go out. This helps them monitor the traffic from all the users. When the hacker logs in, he tries to get into the new computer but is not able to. They notice that he runs _ps -eafg_ command which sets off a flag in Dave’s mind (joke - the flags in the ps command set off a flag in Dave’s mind). Ron from Tymnet gets back, saying that he traced the connection from LBL’s Tymnet port into an Oakland Tymnet office, where someone had dialed in from a telephone. Now, to do a telephone trace, they might need legal orders.
Chapter 7
If they had to ask the phone company to trace the call, they needed an FBI warrant. When they ask the FBI though, they hit a wall since the FBI wants proof that millions of dollars were stolen, and they were wondering why they were bothered by the 75c discrepancy. But they do get the warrant from the Oakland DA’s office. Dave figures out why the flags in the ps command had bothered him. He says the hacker may not be from Berkeley since he was using the old AT&T Unix syntax. The ‘f’ flag is not needed in Berkeley Unix. They find out that the hacker had stolen the password file. Cliff is not worried because the passwords are encrypted using DES algorithm, and breaking that would need enormous computing power.
We now know that DES is not secure. Though AES-128 is mostly used, many sites increasingly use AES-256 to be more secure. I liked this quote - “record observations, apply principles, speculate but trust only proven conclusions”.
Chapter 8
On Wednesday, Cliff finds out that the hacker had connected to the system for around 6 minutes and had connected to Milnet. Milnet was a network that belonged to DoD. By looking up the IP address, Cliff figures out that the computer was in the US Army Depot in Anniston, Alabama. He contacts the admin there to find out that they already knew about an intruder named Hunter. Cliff explains about the security hole and how the hacker might have been using super-user privileges.
Chapter 9
Cliff talks a bit about Berkeley life and about Martha (his girlfriend) and Claudia (their roommate). On Wed, Sep 17, Cliff notices that the previous night, someone was unsuccessfully trying username/password combinations and wonders if there is another hacker. Later, the hacker uses Sventek login and uses Kermit to upload a Trojan horse program (or a mockingbird program as Cliff called it) to steal passwords. It fails because it is designed for AT&T Unix, not Berkeley Unix. The hacker returns to check the file where passwords should have been copied to and finds it empty. He tries the program a few times, gives up, deletes the file and goes away.
Cliff calls the file transfer program Kermit, as the Esperanto of computers. Back in the day (2000s), Java had the reputation of being able to run across platforms. It was marketed as though it would magically work across platforms, but one had to compile the program into bytecode, and the specific machine had to have the OS-specific JVM installed.
Chapter 10
The Tymnet traces led them to Oakland’s Bell telephone exchange, but to have a phone trace, they needed a search warrant. Cliff asks Lee Change the trace specialist at Pac Bell but he says he would not help without a warrant. Sandy Merola, who worked for Roy Kerth, discovers that if you log in from Berkeley library’s public PCs, it would dial Tymnet. They decide to check the library computers when the hacker next logs in. The hacker logs in at noon and Sandy goes to the campus library but finds no one there. So that becomes a dead-end.
The mention that phone lines can be traced only when they are connected, reminded me of many spy-thrillers where this was an essential plot element.
Chapter 11
They finally get the search warrant. They start the trace when the hacker logs in and finds that he logs off immediately. Cliff finds that it is probably because the system operator was seen online and the hacker knows their names/logins by now. So he calls them and asks them to use different pseudonyms. They trace the call to somewhere on the East Coast, possibly Virginia. Cliff says his sister lives there, but this could not be from her. Later, Cliff finds out that though the hacker appeared with Sventek’s login only for 15 mins, he was on the system for over two hours. He was using other dormant accounts - Mark, Goran & Whitberg. He had tried to access three Air Force systems through Milnet using Whitberg’s account and read a few scientific papers.
Two weeks already passed. Cliff had only one more week. I wonder if this would even be possible in modern times. One thing is, when an intruder is detected, usually they are shut down. But there could be hackers exploiting zero-day vulnerabilities and investigators following their trail.
Chapter 12
Cliff gives a short history of the Internet and its evolution from ARPANET. He compares the Internet to the highway traffic system - which works most of the time but has traffic jams, areas with short-term planning, etc. He finds the hacker attempting to access White Sands Missile Range (WSMR) and tells Roy who says that they should alert the authorities immediately. They call the FBI, who turn their backs again since millions of dollars or classified information is not involved. After a few tries, Cliff finally gets on a conference call with Special Agent Jim Christy of the AFOSI (Air Force Office of Special Investigations) and Major Steve Rudd of the Defense Communications Agency. Cliff calls White Sands also and finds out that they are connected to Anniston base that the hacker had logged in to earlier.
Chapter 13
The three-week time that Roy had given was almost up. At the start, it seemed like a lot of time to identify the hacker, but it turned out to be tougher. The hacker connects again, and Cliff coordinates with a bunch of people - Ron Vivier at Tymnet, Lee Cheng at Pac Bell, AT&T technicians in New Jersey and C & P in Virginia. They successfully traced the call to a specific line in Virginia, but the operator there would not give the number to individuals but only to the police. Also, the California search warrant was not valid in Virginia. Roy is out for a couple of weeks, and Cliff contacts the lab’s lawyer, Aletha, who offers to help.
Chapter 14
The next time the hacker logs in, he uses the Goran account. He reads through some emails and then uses NIC to look for CIA contacts. Cliff wonders if he should warn the CIA or not. He is in a dilemma since he has a bad perception of the CIA as spies and hitmen. He decides to call one of the people about whom the hacker pulled information - Ed Manning. Surprisingly, Ed picks up, shows a lot of interest in what Cliff said and tells him that he’d send people over to Berkeley to find out more info. That spooks Cliff and leaves him thinking what his friends would think of him that he is now working with the CIA!
Chapter 15
Four people from CIA arrive at LBL - a driver, Greg Fennel, Teejay and Mr. Big. Dennis Hall, backup for Roy while he is out, tells Cliff to state the facts to the team and not his assumptions. Cliff explains everything to them. Greg, who is the computer expert, asks him many questions. They get interested when Cliff mentions Anniston. Greg clarifies that Dockmaster is not a Navy shipyard but is run by the NSA. Cliff wonders how the CIA knows so much about computers and networking, and Greg tells him that contrary to what people think, the CIA’s main job is information gathering and analysis. Teejay talks about how they caught someone who was involved in a security breach. Cliff asks if he was ‘bumped off’, and Teejay says - “In God we trust, all others we polygraph”. They had wired the hacker to a lie detector, and the FBI had indicted him. Cliff learns that criminal activities within the nation are not under the CIA’s jurisdiction but the FBI’s. Cliff also gets to know that Ed Manning, whom he spoke to, was the director of IT. He hopes Ed could do something to get the FBI to help.
Dennis’s quote - “We’ll always find a few dodos poking around our data. I’m worried about how hackers poison the trust that’s built our networks. After years of trying to hook together a bunch of computers, a few morons can spoil everything.” reminded me that this is true for all emerging technologies. Even the recent advancements around LLM can be misused by a small group of people and potentially ‘spoil everything’.
Chapter 16
The next day, the hacker logs in to the system in the morning around 9. He accesses computers at Anniston Army Depot and prints out a file about the combat readiness of Army missiles. He then tries Ballistic Research Lab’s computers in Maryland but is not able to get through. Later, Cliff finds that he accessed Livermore Laboratory’s MFE network through the ethernet network. During lunch, Cliff meets Luis Alvarez, a Nobel Laureate who advises him to treat the investigation as research where you don’t know what it will cost or how much time it will take, and the only way forward is to keep exploring and continuously going into uncharted territory. After he sees the hacker accessing a computer from MIT’s AI lab, Cliff decides to disconnect the network over the weekend but gets a lot of complaints from users. Also gets a call from Roy Kerth since some folks had escalated to him. He calls someone at MIT to warn them and finds that the hacker had used the login of a plasma scientist and that the machine that was accessed was going to be thrown away.
Chapter 17: Physics and Echoes
The 3-week period to catch the hacker is over. Cliff wonders if he should just plug the hole in his systems and focus on other things, especially because he didn’t hear back from the agencies that he spoke with. That would mean protecting Berkeley’s systems, but the hacker could be infiltrating other high-value targets. Also, what if there is another security hole that he is not aware of, but the hacker is? When he monitors the hacker using the Kermit file transfer program, he wonders why there is a delay in back-and-forth communications. Then it hits him that he could calculate the distance between the hacker and himself using the time taken for round-trip data transfers, like measuring distance using echo. He finds that there is over 3 seconds of round-trip delay in the hacker’s communications. This could mean that the hacker is really far away because even if the hacker were to use a satellite to communicate, you’d need twelve satellite hops to account for a three-second delay. He deduces that the hacker is using networks that move his data inside of packets, and since the packets are constantly being rerouted, assembled, and disassembled, it might account for the time delay. In the end, Cliff is still uncertain whether the hacker is 6000 miles away or somewhere nearby.
Chapter 18: Pseudonyms and Patience
The hacker’s activity becomes more frequent. Cliff connects with Dan Kolkowitz at Stanford, who is dealing with a hacker using the pseudonym “Pfloyd.” A newspaper article in the San Francisco Examiner conflates the Stanford and Berkeley hackers, leading Cliff to fear the intruder will disappear. However, the hacker returns, proving to be methodical and disciplined. Cliff notes that the hacker remembers exactly where he “laid an egg” (a back-door file) in a system three months prior, suggesting this is a professional rather than a “college joker.”
Chapter 19: The Scrabble Connection
Cliff notices the hacker changed all his passwords to “lblhack.” Through a conversation with Maggie Morley, the lab’s document specialist and a Scrabble enthusiast, Cliff learns that the hacker’s previous passwords “Jaeger,” “Hunter,” “Benson,” and “Hedges”, are linked. “Jaeger” is German for “Hunter,” and “Benson & Hedges” is a brand of cigarettes. This insight gives Cliff a humanizing detail: his target is a methodical smoker with a grasp of German!
Chapter 20: The Halloween Trap
On Halloween, when Cliff is just about to go to the party in the evening, the hacker breaks into a new, mismanaged “super-minicomputer” at the lab called the Elxsi. The hacker exploits a wide-open UUCP (Unix-to-Unix Copy) account to gain system privileges. Cliff finally makes it to the party late and dresses up as a Cardinal. Cliff realizes the hacker isn’t a “wizard” but is simply persistent and knows which “unlocked doors” to poke. To keep up with the intruder without living at the lab, Cliff buys a pocket pager and programs his monitors to alert him the moment the hacker logs in.
Chapter 21: The Bureaucratic “Bailiwick”
Cliff begins reaching out to higher-level government agencies, including the Department of Energy (DOE) and the National Security Agency (NSA/NCSC). He is met with a recurring frustration: “bailiwicks.” Every agency expresses interest but claims they lack the jurisdiction or “charter” to actually help or issue a search warrant. Despite the inaction of the “spooks,” Cliff realizes he has become personally responsible for the security of the network community.
Chapter 22: The Virginia Trace
Cliff discovers via a law library computer that he doesn’t actually need a search warrant to trace a call made to his own phone, but the phone companies remain uncooperative. Using fragments of jargon he overheard from a phone technician—”703,” “C and P,” “448-1060”—Cliff and his friends Terry and Jerry deduce the hacker is calling from McLean, Virginia. A clever ruse with a phone operator confirms the number belongs to Mitre Corporation, a defense contractor located just miles from CIA headquarters.
Chapter 23: Reaching Out to Mitre and the CIA
Cliff confirms the Mitre connection by “trading” astronomical posters to a phone technician for a verbal confirmation of the trace. He contacts Mitre’s security officer, Bill Chandler, who is skeptical that a secure site could be the source of a breach. Cliff also calls “Teejay” at the CIA, who is shocked by the Mitre lead but maintains that the CIA cannot involve itself in domestic affairs. Finally, the Air Force Office of Special Investigations (OSI) takes an interest, realizing that the path is leading toward high-level defense and intelligence targets in Virginia.
- Chapter 24
- Chapter 25
- Chapter 26
- Chapter 27
- Chapter 28
- Chapter 29
- Chapter 30
- Chapter 31
- Chapter 32
- Chapter 33
- Chapter 34
- Chapter 35
- Chapter 36
- Chapter 37
- Chapter 38
- Chapter 39
- Chapter 40
- Chapter 41
- Chapter 42
- Chapter 43
- Chapter 44
- Chapter 45
- Chapter 46
- Chapter 47
- Chapter 48
- Chapter 49
- Chapter 50
- Chapter 51
- Chapter 52
- Chapter 53
- Chapter 54
- Chapter 55
- Chapter 56
- Epilogue
Misc
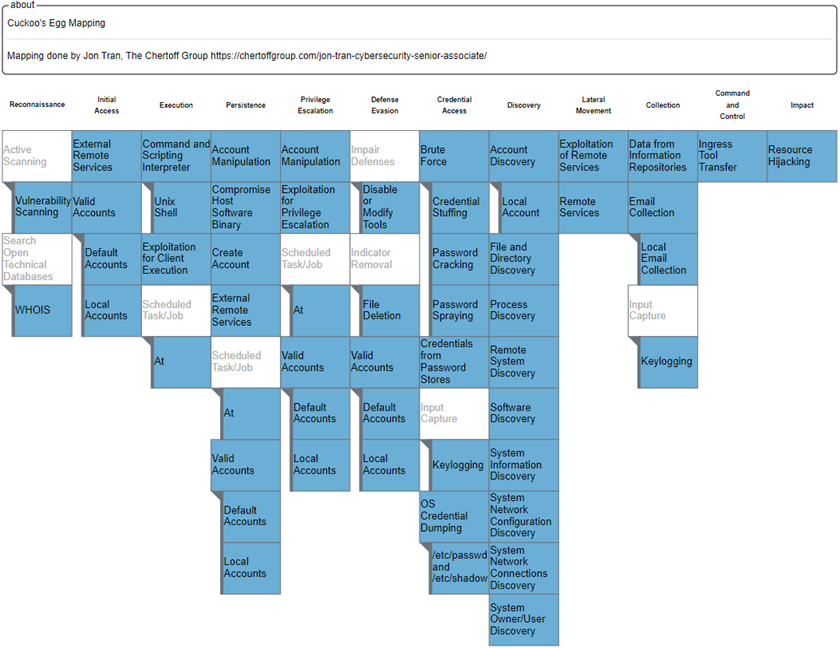
Chapter 23 - Mitre Corporation - The MITRE ATT&CK framework is a modern knowledge base of cyber adversary behaviors developed by the same MITRE Corporation.
- Evolution: Launched internally in 2013 and released publicly in 2015, the framework grew out of a research project called the Fort Meade Experiment (FMX). https://www.ibm.com/think/topics/mitre-attack
The Cuckoos Egg - MITRE ATT&CK Mapping - https://chertoffgroup.com/mapping-the-cuckoos-egg/
Kindle Highlights / Readwise
- I wore the standard Berkeley corporate uniform: grubby shirt, faded jeans, long hair, and cheap sneakers. Managers occasionally wore ties, but productivity went down on the days they did. (Location 93)
- Now, an error of a few thousand dollars is obvious and isn’t hard to find. But errors in the pennies column arise from deeply buried problems, (Location 104)
- Big computers have two types of software: user programs and systems software. (Location 193)
- Not dull software engineers who put in forty hours a week, but creative programmers who can’t leave the computer until the machine’s satisfied. A hacker identifies with the computer, knowing it like a friend. (Location 209)
- the best part of working at Lawrence Berkeley Labs was the open, academic atmosphere. (Location 233)
- with no connections to the outside, Livermore’s computers can’t be dialed into. Their classified data’s protected by brute force: isolation. (Location 235)
- Different operating systems have various names for privileged accounts—super-user, root, system manager—but these accounts must always be jealously guarded against outsiders. (Location 263)
- Our computer center’s nestled between three particle accelerators: the 184-inch cyclotron, where Ernest Lawrence first purified a milligram of fissionable uranium; the Bevatron, where the anti-proton was discovered; and the Hilac, the birthplace of a half-dozen new elements. (Location 280)
- both laboratories are named after California’s first Nobel Laureate, both are centers for atomic physics, and both are funded by the Atomic Energy Commission’s offspring, the Department of Energy. (Location 290)
- Since their computers are often the first ones off the production line, Livermore usually has to write their own operating systems, forming a bizarre software ecology, unseen outside of their laboratory. Such are the costs of living in a classified world. (Location 307)
- By trusting his users, he ran an open system and devoted his time to improving their software, instead of building locks. (Location 326)
- Collect raw data and throw away the expected. What remains challenges your theories. (Location 390)
- The daemons themselves are just programs that copy data from the outside world into the operating system—the eyes and ears of Unix. (The ancient Greek daemons were inferior divinities, midway between gods and men. In that sense, my daemons are midway between the god-like operating system and the world of terminals and disks.) (Location 410)
- The cuckoo lays her eggs in other birds’ nests. She is a nesting parasite: some other bird will raise her young cuckoos. The survival of cuckoo chicks depends on the ignorance of other species. (Location 461)
- Richard Stallman, a free-lance computer programmer, loudly proclaimed that information should be free. His software, which he gives away for free, is brilliantly conceived, elegantly written, and addictive. (Location 474)
- Gnu was the hole in our system’s security. A subtle bug in an obscure section of some popular software. (Location 488)
- The hacker had fun, even if Ed didn’t. (Location 515)
- Often, these networked computers had been arranged to trust each other. If you’re OK on that computer, then you’re OK on this one. This saved a bit of time: people wouldn’t need to present more than one password when using several computers. (Location 522)
- The astronomer’s rule of thumb: if you don’t write it down, it didn’t happen. (Location 537)
- The price of hard evidence was hard work. (Location 577)
- Living together was different. We were both free. We freely chose to share each day, and either of us could leave if the relationship was no longer good for us. (Location 600)
- Physics: there was the key. Record your observations. Apply physical principles. Speculate, but only trust proven conclusions. (Location 767)
- Tags: favorite
- Somebody’s always had control over information, and others have always tried to steal it. Read Machiavelli. As technology changes, sneakiness finds new expressions.” (Location 849)
- Instead of writing five different, incompatible programs, he created a single standard to exchange files between any systems. Kermit’s become the Esperanto of computers. (Location 874)
- Was this program a Trojan horse? Maybe I should call it a mockingbird: a false program that sounded like the real thing. (Location 901)
- If everyone used the same version of the same operating system, a single security hole would let hackers into all the computers. Instead, there’s a multitude of operating systems: Berkeley Unix, AT&T Unix, DEC’s VMS, IBM’s TSO, VM, DOS, even Macintoshes and Ataris. This variety of software meant that no single attack could succeed against all systems. (Location 931)
- Just like genetic diversity, which prevents an epidemic from wiping out a whole species at once, diversity in software is a good thing. (Location 933)
- Our networks form neighborhoods, each with a sense of community. (Location 1137)
- Most networks are so complicated and interwoven that no one knows where all their connections lead, (Location 1147)
- asked what cops were in charge of the Internet. (Location 1209)
- To Dennis, size is measured by counting computers on your network; speed is measured in megabytes per second—how fast the computers talk to each other. The system isn’t the computer, it’s the network. (Location 1429)
- “We’ll always find a few dodos poking around our data. I’m worried about how hackers poison the trust that’s built our networks. After years of trying to hook together a bunch of computers, a few morons can spoil everything.” (Location 1431)
- When you’re doing real research, you never know what it’ll cost, how much time it’ll take, or what you’ll find. You just know there’s unexplored territory and a chance to discover what’s out there.” (Location 1639)
- Nobody will pay for research; they’re only interested in results,” (Location 1653)
- The echoes tell you how far the sound traveled. To find the distance to the canyon wall, just multiply the echo delay by half the speed of sound. (Location 1726)
- “People want to share information, so they make most of the files readable to everyone on their computer. They complain if we force them to change their passwords. Yet they demand that their data be private.” (Location 1774)
- People paid more attention to locking their cars than securing their data. (Location 1776)
- But he hadn’t changed any of the system passwords like Bin, since he assumed he was the only one who knew them. (Location 1835)
- A kid on a weekend lark doesn’t keep detailed notes. A college joker won’t patiently wait three months before checking his prank. No, we were watching a deliberate, methodical attack, from someone who knew exactly what he was doing. (Location 1842)
- “You can hitch a thousand chickens to your plow or one horse. Central computing is expensive because we deliver results, not hardware.” (Location 1893)
- “Breaking into a California computer isn’t a crime in Virginia.” (Location 1909)
- Elxsi had its UUCP account set up with system privileges. It took the hacker only a minute to realize that he’d stumbled into a privileged account. (Location 1960)
- This guy wasn’t the problem. Elxsi was. They sold their computers with the security features disabled. After you buy their machine, it’s up to you to secure it. (Location 2002)
- The hacker didn’t succeed through sophistication. Rather he poked at obvious places, trying to enter through unlocked doors. Persistence, not wizardry, let him through. (Location 2005)
- Commission. Perhaps nuclear bombs and atomic power plants are fading into the mists of history, or maybe splitting atoms isn’t as sexy as it used to be. (Location 2021)
- My networks were as essential to the lab as steam, water, or electricity. (Location 2070)
- The networks were no more mine than the steam pipes belonged to the plumbers. But someone had to treat them as his own, and fix the leaks. (Location 2071)
- The network community depended on me, without even knowing it. Was I becoming (oh, no!) responsible? (Location 2078)
- Indeed, some telephone companies now sell phones that display the digits of the calling telephone as your phone is ringing. (Location 2090)
- Back in graduate school, I’d learned how to survive without funding, power, or even office space. Grad students are lowest in the academic hierarchy, and so they have to squeeze resources from between the cracks. When you’re last on the list for telescope time, you make your observations by hanging around the mountaintop, waiting for a slice of time between other observers. When you need an electronic gizmo in the lab, you borrow it in the evening, use it all night, and return it before anyone notices. (Location 2135)
- Well, the CIA was interested, but not much help. Time to call the FBI. For the seventh time, the Oakland FBI office didn’t raise an eyebrow. The agent there seemed more interested in how I traced the call than in where it led. (Location 2190)
- back. Eventually, we concluded that it’s just not possible for someone in one part of the federal bureaucracy to officially thank someone in another.) (Location 2254)
- Did he know something that I didn’t? Did this hacker have a magic decryption formula? Unlikely. If you turn the crank of a sausage machine backwards, pigs won’t come out the other end. (Location 2616)
- He grew up in Dorset, England, and first learned to program a computer by mail: he’d write a program at school, send it to a computer center, and receive the printout a week later. (Location 2764)
- I wondered how a real professional would track this hacker. But then, who were the professionals? Was anyone dedicated to following people breaking into computers? I hadn’t met them. (Location 3208)
- Saved by my logbook. (Location 3354)
- If you don’t document it, you might as well not have observed (Location 3354)
- The bureaucrats might not be able to communicate with each other, but the technicians sure did. (Location 3722)
- High security computers are difficult to get onto, and unfriendly to use. Open, friendly systems are usually insecure. (Location 4466)
- “Any system can be insecure. All you have to do is stupidly manage it.” (Location 4577)
- the shoemakers’ kids are running around barefoot. (Location 5239)
- took advantage of administrators’ blunders. Leaving accounts protected by obvious passwords. Mailing passwords to each other. Not monitoring audit trails. (Location 5243)
- For a year, the chase had consumed my life. In the course of my quest, I’d written dozens of programs, forsaken the company of my sweetheart, mingled with the FBI, NSA, OSI, and CIA, nuked my sneakers, pilfered printers, and made several coast-to-coast flights. I pondered how I would now spend my time, now that my life wasn’t scheduled (Location 5397)
- That’s the problem with talking about security problems. If you describe how to make a pipe bomb, the next kid that finds some charcoal and saltpeter will become a terrorist. Yet if you suppress the information, people won’t know the danger. (Location 5535)